| Category | Information |
|---|---|
| Definition | Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. It's used to remotely access and manage devices. |
| Importance in IoT | Essential for remote monitoring, management, software updates, and troubleshooting of IoT devices. |
| Security Risks | Default passwords, weak encryption, unpatched vulnerabilities, and unauthorized access. |
| Best Practices | Strong passwords, SSH key-based authentication, disabling password authentication, regular security audits, and keeping software up-to-date. |
| Common Use Cases | Remote device monitoring, software updates, configuration management, troubleshooting, and security patching. |
| Vulnerability Management | Regularly scan for vulnerabilities, apply security patches promptly, and implement intrusion detection systems. |
| Authentication Methods | Password-based authentication, SSH key-based authentication (recommended). |
| Key Management | Securely generate, store, and manage SSH keys. |
| Access Control | Limit SSH access to authorized users and devices only. |
| Monitoring and Logging | Monitor SSH login attempts and log all activities for auditing purposes. |
| Tools and Solutions | OpenSSH, SocketXP, various SSH clients (PuTTY, OpenSSH client). |
| Reference | SSH.com |
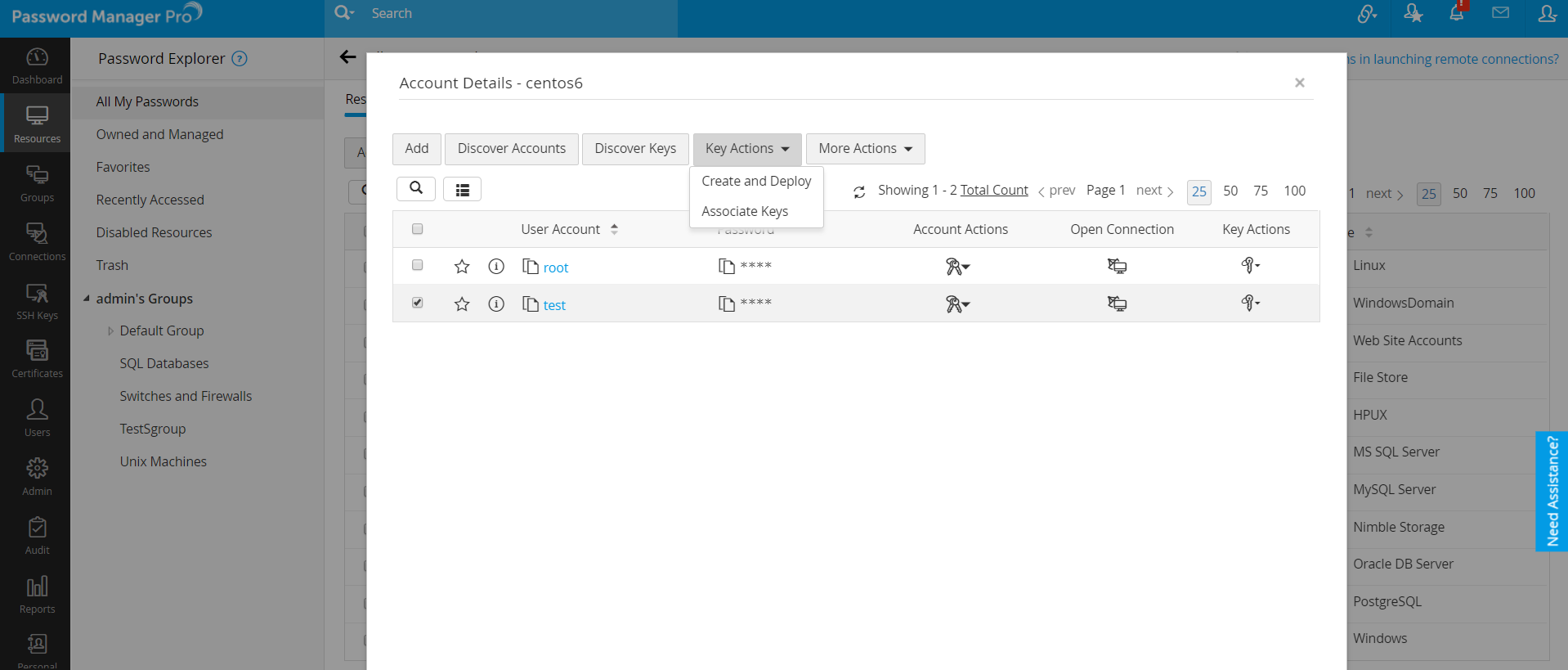
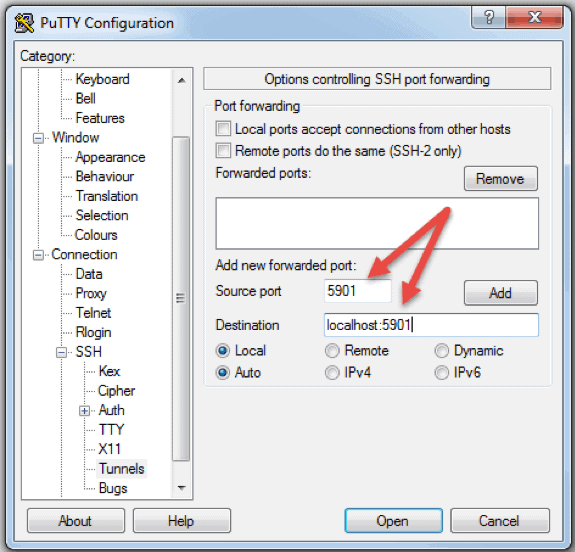
Remote SSH login empowers IoT deployments in numerous ways. One of the most crucial applications is the ability to keep IoT devices running the latest software versions. Regular software updates are essential for patching security vulnerabilities and improving device performance. Remotely logging into a device via SSH allows administrators to deploy these updates quickly and efficiently, minimizing downtime and reducing the risk of exploitation. Furthermore, SSH facilitates remote monitoring and management of devices, providing administrators with real-time insights into device performance and status. This helps in identifying and resolving issues proactively, ensuring optimal device operation. In the realm of IoT android development, remote SSH login has become an indispensable skill for developers and tech enthusiasts alike. It enables them to debug applications, configure devices, and perform other essential tasks remotely. The versatility and security of SSH make it an invaluable tool for managing and maintaining IoT devices across a wide range of applications. In todays interconnected world, the management of remote SSH login IoT passwords has emerged as a critical factor in safeguarding the security and functionality of IoT devices. The use of default passwords or weak passwords can expose devices to unauthorized access and control. Attackers can easily exploit these vulnerabilities to compromise devices, steal sensitive data, or even disrupt critical services. Therefore, it is imperative to implement strong password policies and enforce regular password changes. Moreover, organizations should consider disabling password-based SSH authentication altogether and instead rely on SSH key-based authentication. This method provides a much higher level of security by eliminating the need for passwords, which can be easily intercepted or cracked. By adopting secure password practices and implementing robust authentication mechanisms, organizations can significantly reduce the risk of unauthorized access and ensure the integrity of their IoT infrastructure. Disabling password-based SSH authentication and enabling SSH key-based authentication for SSH login dramatically enhances the security of remote access to IoT devices. SSH keys are cryptographic key pairs that provide a more secure way to authenticate users. Instead of relying on passwords, which can be compromised, SSH keys use a private key stored on the user's device and a public key stored on the server. When a user attempts to log in, the server verifies the user's identity by checking if the private key matches the public key. This process is much more secure than password-based authentication because it is extremely difficult for attackers to forge or steal SSH keys. To implement SSH key-based authentication, you first need to generate a key pair. If you do not have a key, you can create one using the `ssh-keygen` command. Once the key pair is generated, you need to authorize the public key on the remote host by copying it to the `~/.ssh/authorized_keys` file. From now on, SSH access to the device will no longer require a password, significantly improving security. OpenSSH server and client software, when combined with a powerful IoT remote access solution like SocketXP, provides an excellent framework for managing and maintaining your IoT device fleet remotely. OpenSSH is a widely used and trusted implementation of the SSH protocol, providing secure encryption and authentication. SocketXP extends the capabilities of OpenSSH by providing a cloud-based platform for managing remote access to IoT devices. This combination allows administrators to securely connect to devices behind firewalls and NATs, simplifying remote management and troubleshooting. To get started, you need to follow a few simple steps. First, download and install the SocketXP IoT agent on your IoT device. The agent acts as a secure tunnel, allowing you to connect to the device remotely. Next, configure the agent to connect to the SocketXP cloud platform. Once the agent is installed and configured, you can access your IoT device from anywhere in the world using the SocketXP client software. This combination of OpenSSH and SocketXP provides a secure, reliable, and scalable solution for managing your IoT device fleet remotely. One crucial step in securing remote SSH login for IoT devices is ensuring that only authorized devices can SSH into the IoT device. This can be achieved by implementing access control lists (ACLs) or firewall rules that restrict SSH access to specific IP addresses or networks. By limiting access to authorized devices only, you can significantly reduce the risk of unauthorized access and prevent attackers from gaining control of your IoT devices. This is particularly important in environments where multiple devices share the same network. Without proper access controls, an attacker could compromise one device and then use it as a springboard to attack other devices on the network. Implementing access control lists is a simple but effective way to enhance the security of your IoT infrastructure. This step ensures that only trusted devices can establish an SSH connection to your IoT device, minimizing the attack surface and reducing the risk of unauthorized access. Once all the preparations are complete, its time to test the SSH connection to ensure that everything is working as expected. Open your SSH client, such as PuTTY or the OpenSSH client, and enter the IP address of the IoT device, along with your username. If you have enabled password-based authentication, you will be prompted to enter your password. If you have enabled SSH key-based authentication, the SSH client will automatically authenticate you using your private key. If the connection is successful, you will be presented with a command prompt on the IoT device. You can then execute commands and perform other administrative tasks remotely. It is important to verify that you can successfully connect to the device and that you have the necessary privileges to perform the required tasks. This testing process ensures that the SSH configuration is correct and that you can securely access and manage your IoT device remotely. To further enhance the security of remote SSH login for IoT devices, it is essential to use strong, unique passwords and SSH keys. Weak or easily guessable passwords are a common target for attackers, who can use brute-force attacks or dictionary attacks to crack them. Therefore, it is imperative to use strong passwords that are at least 12 characters long and contain a mix of uppercase and lowercase letters, numbers, and symbols. Additionally, it is important to avoid using the same password for multiple devices or accounts. If one password is compromised, all devices and accounts that use the same password will be at risk. Similarly, it is crucial to use strong SSH keys that are at least 2048 bits long. Shorter keys are more vulnerable to attack. By using strong passwords and SSH keys, you can significantly increase the difficulty for attackers to gain unauthorized access to your IoT devices. Regular password and key rotation is also recommended to further enhance security. To help you navigate this critical topic, this article explores the best practices, tools, and strategies for implementing remote SSH login for IoT devices. We have discussed the importance of strong passwords, SSH key-based authentication, access control lists, and other security measures. By following these best practices, you can significantly reduce the risk of unauthorized access and ensure the integrity of your IoT infrastructure. In addition to the techniques discussed in this article, it is also important to keep your software up-to-date with the latest security patches. Vulnerabilities in SSH server and client software are often discovered and exploited by attackers. Therefore, it is essential to regularly update your software to patch these vulnerabilities. Furthermore, you should implement intrusion detection systems to monitor your network for suspicious activity. Intrusion detection systems can help you identify and respond to attacks in real-time, minimizing the damage caused by unauthorized access. By mastering remote SSH login and adopting secure password practices, you can significantly reduce the risk of unauthorized access and ensure the integrity of your IoT infrastructure. The remote SSH connection for IoT devices is commonly used in three scenarios. The first is remote monitoring and management of devices, which helps administrators keep an eye on the performance and status of devices. Secondly, remote SSH login allows for the deployment of software updates and security patches. Finally, it is used for troubleshooting and diagnostics, enabling administrators to identify and resolve issues remotely. This helps administrators to keep an eye on the performance and status of devices. Whether youre managing a single smart device or a vast network of industrial sensors, secure remote access is essential for ensuring the reliability, security, and functionality of your IoT ecosystem. Therefore, it is imperative to invest in the necessary tools and expertise to implement robust security measures for remote SSH login. As IoT ecosystems continue to expand, the need for secure remote access becomes even more pronounced. With the increasing number of connected devices, the attack surface for cybercriminals is also growing. Therefore, it is essential to stay ahead of the curve and implement proactive security measures to protect your IoT infrastructure. This includes not only securing remote SSH login but also implementing other security controls such as network segmentation, encryption, and multi-factor authentication. One particularly powerful tool in this realm is the secure shell (SSH), a network protocol that provides secure remote access over an insecure network. However, using SSH with IoT devices via the internet requires careful consideration of security implications. It is crucial to implement the best practices discussed in this article to ensure that your IoT devices are protected from unauthorized access and cyberattacks. By taking a proactive and security-conscious approach, you can confidently deploy and manage your IoT devices, knowing that they are protected by robust security measures.

Detail Author:
- Name : Maritza Marks
- Username : destiney.gerlach
- Email : rasheed54@spinka.com
- Birthdate : 1988-12-24
- Address : 867 Kayli Point Apt. 190 Arelyland, ID 52098-0605
- Phone : 681.390.0264
- Company : Dibbert-Walsh
- Job : Executive Secretary
- Bio : Possimus totam similique non. At perferendis non sint omnis sapiente minima. Voluptatem architecto dolorum et quasi asperiores quia dolor. Neque minus dolorem eligendi nulla qui.
Socials
facebook:
- url : https://facebook.com/tyrell4268
- username : tyrell4268
- bio : Voluptatibus officiis et veniam quia qui dolores quam.
- followers : 1921
- following : 501
linkedin:
- url : https://linkedin.com/in/tyrell.homenick
- username : tyrell.homenick
- bio : Omnis quo aliquam est assumenda ab aut.
- followers : 6987
- following : 2715